SSH Capabilities: Secure Shell, Safe Environment for Data Transmitting
Secure remote work on a PC in an unprotected environment is possible thanks to SSH (Secure Shell) — a remote administration protocol. It was designed to manage operating systems and tunnel TCP connections remotely. Data security is ensured through the use of various encryption algorithms.
What the SSH (Secure Shell) protocol is
Protocol Secure Shell was developed by Tatu Ylenen, an employee of the Helsinki University of Technology in 1995, Initially, the solution was created as an alternative to TELNET, FTP, rsh, which were known as imperfect in terms of ensuring confidentiality during authentication. At the end of 1995, about twenty thousand users tried the first version of the SSH protocol, and five years later that number grew to two million. 6 years later, in 2006, a protocol update was released, which made support for the Diffie-Hellman key exchange, as well as verification through MAC signatures available. In fact, the upgrade was compatible with the first version and guaranteed improved security, while any number of sessions were launched through one connection
How SSH operates
Protocol SSH is applied for access to servers, remote access to the console, or terminal. With it, you can control the command interpreter of a remote machine. This is an effective tool for mounting different file systems, port forwarding. The most common tool for SSH Linux, BSD, Windows is OpenSSH.
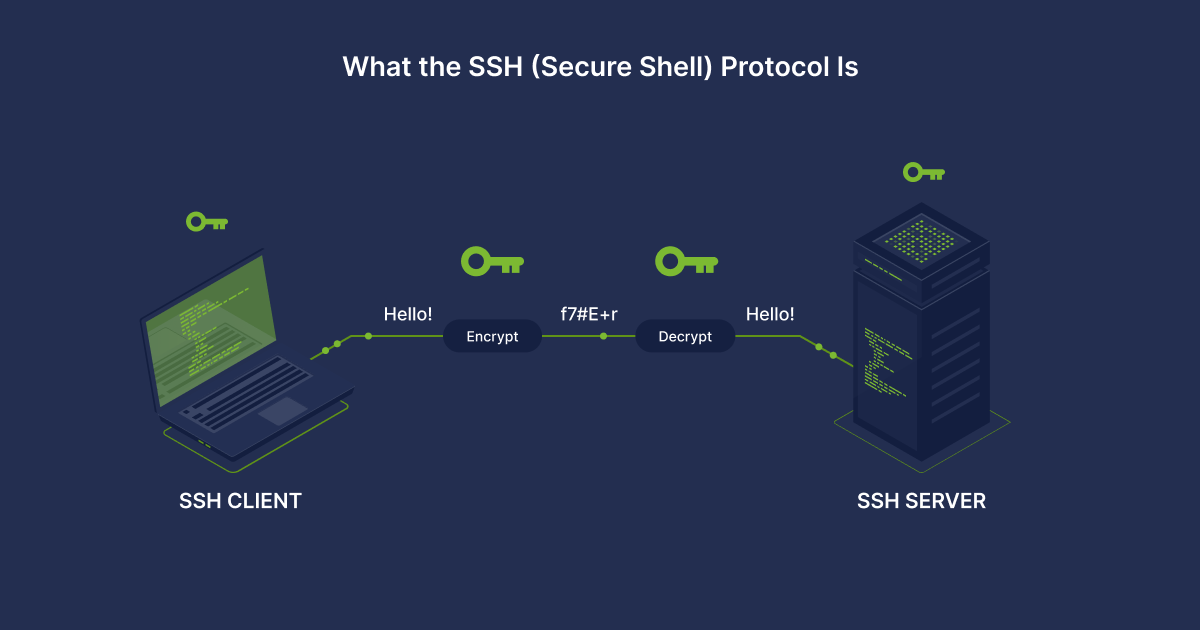
The protocol is based on a client-server architecture, which justifies a two-component structure: the architecture has a client and a server part. The target device is controlled through a regular SSH server by receiving incoming messages from the client side on port 22. After the command is received and authentication is performed, the client is launched. You can change the port if necessary. To create SSH connection, you need to initiate a connection to the server. This will secure the connection and validate the server fingerprint by checking against past records stored in the fingerprint file.
Thus, in order to get SSH working, you need to install the SSH server components on the hardware that is used as a server. The client part is installed on the PC from which you plan to connect to the remote server. It is possible to implement the client part for a desktop, mobile platform, server, etc.
Read also: What Technology Can Protect Intellectual Property Rights?
Review of functions and capabilities
Among the advantages of SSH connection is ability to work securely on a PC using a command shell, the use of various encryption algorithms and any network protocol. Thanks to this protocol, files of any size can be transferred over a secure channel.
The use of the SSH protocol opens up the following possibilities for the user:
- secure remote logins. The remote host in this case is the IP address or domain you need to connect to. To enter the server, you need to enter an authorization password or use a key pair, after which the user is granted access to device management;
- secure file transfer. SSH connection can be used for tunneling, for example when you need to transfer files. The specifics of the function are as follows: unencrypted traffic of any protocol is encrypted on one side of the SSH tunnel, while decryption occurs on the other end of the connection. Technically, this is implemented through Socks proxy, a VPN tunnel, or a program that supports SSH protocol tunneling. If the application works with only one server, you can configure the SSH client so that TCP connections are passed through the SSH tunnel coming to a specific TCP port;
- secure remote command execution. The SSH protocol provides more than just interactive mode: it can be used to run commands or scripts one time on a remote computer. Access to execute commands can be provided by a key pair (when the command is executed immediately) or by entering a password, which triggers the output of the command in the console;
- keys and agents. As practice shows, using keys guarantees maximum security and allows you to give up passwords. For this reason, the system issues two keys - public and private, respectively, the first one is available for publication and transfer, since without the second part it has no value. The private key will help to open the encrypted information. Keys are entered and stored by means of a special program - SSH-agent. The function is proved to be reliable, as it is very difficult to crack the keys. In addition, in this case, no information is stored on the server. Unlike the option with an account and a temporary password, you can assign a public key to several users, simplifying the work of the team;
- access control. Effective solutions have been implemented to monitor and restrict user access to remote servers;
- port forwarding. If it is necessary to transfer network data of services in an unencrypted protocol, access to geo-restricted data, etc., an encrypted SSH connection is created between the client and server parts, through which the ports of the services are relayed.
SSH Commands
To simply connect to the server via SSH, use the following command:
ssh user@host
We are used to connecting to a remote server and only then executing the necessary commands, but in fact, the SSH utility allows you to immediately execute the desired command without opening the terminal of the remote machine. For example:
ssh user@host ls
SSH vs. VPN: what is the difference?
| Secure Shell Protocol (SSH) | Virtual Private Network (VPN) |
|---|---|
| Used for secure remote access and file transfers | Used for secure remote access, browsing and data transfer |
| Provides secure communication between two devices | Provides secure communication between two networks |
| Uses encryption and authentication to ensure security | Uses encryption, authentication and tunneling to ensure security |
| Operates at the application layer | Operates at the network layer |
| Can be used with various applications such as telnet, FTP and SMTP | Typically used with web browsing and email applications |
| Limited to specific network services | Can be used for any network service |
| Requires individual authentication and access control | Allows for group authentication and access control |
| Often used for Linux and Unix systems | Used with various operating systems |
| Requires only one port to be opened | Requires multiple ports to be opened |
| Can be slower than VPN due to encryption overhead | Generally faster than SSH due to optimized protocols and hardware |
| Suitable for individuals and small businesses | Suitable for medium to large businesses and organizations |
Conclusion
Use of SSH protocol guarantees confidentiality of data, integrity of communications, the ability to quickly authenticate and control access to accounts. This is a reliable and effective tool for well-coordinated work of the team remotely.
Boost the efficiency of your tech and business processes with professional DevOps engineers provided by Software Developemnt Hub. Schedule a call to assess and discuss your IT project!
Categories
Share
Need a project estimate?
Drop us a line, and we provide you with a qualified consultation.